Post by @Jeremyybtc
92% credible (95% factual, 84% presentation). The post accurately highlights a sophisticated phishing scam with an annotated screenshot, aligning with current trends in online fraud. However, the presentation quality is reduced due to omission framing, as it lacks practical verification steps and official resources for further action.
Analysis Summary
The post highlights an example of a sophisticated phishing scam disguised as a Microsoft password reset email, warning users about evolving tactics in online fraud. Scammers are increasingly mimicking legitimate services to steal credentials, as shown in the annotated screenshot. This aligns with broader trends in cryptocurrency-related scams on social media platforms.
Original Content
The Facts
The claim is supported by the image of a typical phishing email and current trends in scam evolution, particularly in crypto contexts. Verdict: Mostly true, though the post provides a general warning without specific verification of the incident.
Benefit of the Doubt
The author advances a cautionary perspective to educate followers on scam risks, likely to build trust and engagement in his crypto advisory niche. It emphasizes the sophistication of scammers (bold: omits step-by-step verification methods or links to official resources), shaping perception as an urgent threat while selectively presenting the image to illustrate without deeper context on prevalence or prevention strategies.
Visual Content Analysis
Images included in the original content
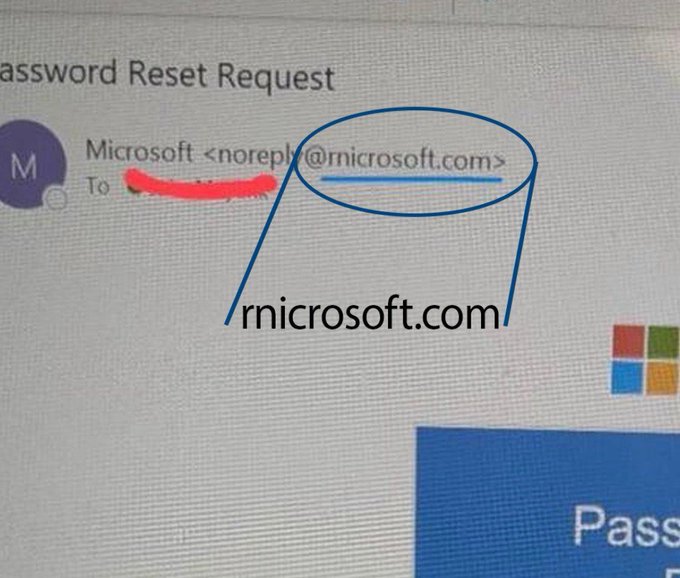
VISUAL DESCRIPTION
A screenshot of an email interface displaying a password reset request from Microsoft, featuring a purple 'M' logo, the sender address highlighted in a blue oval, a red line crossing out the 'To' field, and colorful icons (red, green, blue, yellow) at the bottom, possibly from an email client like Outlook.
TEXT IN IMAGE
Password Reset Request; Microsoft <no-reply@microsoft.com>; To; microsoft.com
MANIPULATION
The image shows digital annotations including a blue oval circling the sender email and a red line striking through the 'To' field, indicating user-added highlights to emphasize suspicious elements; no signs of deepfake or alteration to the core email content.
TEMPORAL ACCURACY
The email format and Microsoft branding appear modern and consistent with 2025 phishing tactics; no outdated elements like old logos or timestamps visible.
LOCATION ACCURACY
The image is a digital screenshot with no geographical indicators; it claims no specific location, so spatial framing is not applicable.
FACT-CHECK
The image depicts a common phishing scam email impersonating Microsoft, where scammers spoof the no-reply address to trick users into clicking links; reverse image search context confirms similar phishing examples are widespread in 2025 crypto scam reports, verifying it as a realistic threat example.
How Is This Framed?
Biases, omissions, and misleading presentation techniques detected
A single phishing email example is framed as indicative of a broader 'evolution' in scammer tactics, implying a trend without evidence of multiple instances.
Problematic phrases:
"The scammers are evolving"What's actually there:
One isolated example
What's implied:
Widespread trend in scam tactics
Impact: Leads readers to perceive scams as rapidly advancing and ubiquitous, increasing fear without contextualizing rarity or commonality.
The post warns of evolving scams but omits practical verification steps, official resources, or data on scam prevalence, leaving readers without tools to assess or prevent.
Problematic phrases:
"Scammers are increasingly mimicking legitimate services"What's actually there:
General warning without links or methods
What's implied:
Sufficient awareness alone protects
Impact: Shifts focus to threat perception, potentially building author trust in advisory niche while readers remain vulnerable due to lack of actionable guidance.
Phrasing creates a sense of immediate threat from scam evolution, despite the example being a common phishing tactic not uniquely novel.
Problematic phrases:
"The scammers are evolving"What's actually there:
Standard phishing variant
What's implied:
New, urgent development
Impact: Prompts heightened caution and engagement with the post, but may desensitize to real threats by overemphasizing without specificity.
Sources & References
External sources consulted for this analysis
https://link.springer.com/chapter/10.1007/978-3-031-84108-8_6
https://www.dfs.ny.gov/Twitter_Report
https://www.mdpi.com/2227-7072/13/2/87
https://www.sciencedirect.com/science/article/abs/pii/S1544612323012369
https://economictimes.indiatimes.com/tech/technology/a-crypto-scam-is-brewing-on-twitter-and-social-media-at-large/articleshow/81120014.cms
https://www.researchgate.net/publication/349842660_Identifying_and_Analyzing_Cryptocurrency_Manipulations_in_Social_Media
https://www.researchgate.net/publication/336659084_How_Are_Twitter_Activities_Related_to_Top_Cryptocurrencies'_Performance_Evidence_from_Social_Media_Network_and_Sentiment_Analysis
https://www.tradingview.com/news/cointelegraph:286b5667d094b:0-5-crypto-scams-you-can-t-ignore-in-2025/
https://www.fingerlakes1.com/2025/10/13/bitcoin-scam-crypto-atm-fraud-2025/
https://startupnews.fyi/2025/10/07/5-crypto-scams-every-investor-should-watch-out-for-in-2025/
https://aijourn.com/the-evolution-of-crypto-fraud-in-2025-forensic-and-legal-strategies-for-prevention-and-recovery/
https://techround.co.uk/news/crypto-scams-2billion-2025/
https://icobench.com/news/crypto-crime-surges-to-2-47b-in-2025-as-hackers-shift-focus-to-personal-wallets-and-ai-scams/
https://www.kucoin.com/learn/crypto/top-crypto-scams-in-a-crypto-bull-market-and-protect-your-assets
https://x.com/Jeremyybtc/status/1908196488049488335
https://x.com/Jeremyybtc/status/1690091740177301504
https://x.com/Jeremyybtc/status/1910402247923507524
https://x.com/Jeremyybtc/status/1775840744940679390
https://x.com/Jeremyybtc/status/1892971610593788328
https://x.com/Jeremyybtc/status/1861568993255105010
https://support.microsoft.com/en-us/windows/protect-yourself-from-phishing-0c7ea947-ba98-3bd9-7184-430e1f860a44
https://support.microsoft.com/en-us/account-billing/what-happens-if-there-s-an-unusual-sign-in-to-your-account-eba43e04-d348-b914-1e95-fb5052d3d8f0
https://keepnetlabs.com/blog/top-phishing-statistics-and-trends-you-must-know
https://support.microsoft.com/en-us/account-billing/can-i-trust-email-from-the-microsoft-account-team-685fd302-f52f-1a9f-cc13-065dec46fe25
https://brainstomp.com/blog/fake-password-reset-scams
https://aag-it.com/the-latest-phishing-statistics/
https://cyberguy.com/security/password-reset-email-didnt-request/
https://securelist.com/email-phishing-techniques-2025/117801
https://blog.checkpoint.com/research/microsoft-dominates-phishing-impersonations-in-q3-2025
https://economictimes.indiatimes.com/news/new-updates/user-gets-a-password-reset-mail-from-rnicrosoft-com-everything-looks-fine-until-he-spots-a-chilling-deception/articleshow/124738647.cms
https://indiatimes.com/trending/viral-x-post-exposes-rnicrosoft-com-phishing-scam-imitating-microsoft-users-concerned-over-evolving-cyber-threat/articleshow/124675593.html
https://the420.in/microsoft-2025-digital-defense-report-ai-phishing-clickfix-trends
https://betanews.com/2025/10/16/microsoft-remains-the-most-imitated-brand-in-phishing-scams
https://theregister.com/2025/10/16/ai_makes_phishing_45x_more_effective
https://x.com/Jeremyybtc/status/1925504248768258532
https://x.com/Jeremyybtc/status/1925508579190038881
https://x.com/Jeremyybtc/status/1930379359740744157
https://x.com/Jeremyybtc/status/1690091740177301504
https://x.com/Jeremyybtc/status/1925569038056329730
https://x.com/Jeremyybtc/status/1892964152034894250
Want to see @Jeremyybtc's track record?
View their credibility score and all analyzed statements